Prerequisites for a Private Access Channel
Before you configure a private access channel, you need to know the domain names of the private DNS zones or SCAN host names you want Oracle Analytics Cloud to access, check that you deployed Oracle Analytics Cloud with Enterprise Edition, and verify you have the correct permissions.
If your Oracle Analytics Cloud is deployed with a public endpoint, you also need to know the VCN and subnet on Oracle Cloud Infrastructure that you want Oracle Analytics Cloud to use to access the private sources. If you deployed Oracle Analytics Cloud instance with a private endpoint, the private access channel automatically uses the same VCN and subnet you configured for the instance so you don't need to do step 3.
- Verify that your Oracle
Analytics Cloud deployment includes Enterprise Edition.
Edition information is displayed on the Instance Details page. See Verify Your Service.
Private access channels aren't available on Oracle Analytics Cloud instances deployed with Professional Edition.
- Record the domain name of each private source (DNS zone) you want Oracle
Analytics Cloud to access through the private channel.
For example, domain names such as
example.com,companyabc.com, and so on.-
Private data source in a corporate network peered to an Oracle Cloud Infrastructure VCN
Register a DNS zone in the format:
<domain name>For example:
- If the data source FQDN hostname is
data-source-ds01.companyabc.com, add the DNS Zone ascompanyabc.com. - If the data source FQDN hostname is
db01.dbdomain.companyabc.com, add the DNS Zone asdbdomain.companyabc.comto only give Oracle Analytics Cloud access to hosts underdbdomain.companyabc.com.
- If the data source FQDN hostname is
-
Private data source in an Oracle Cloud Infrastructure VCN
Register a DNS zone in the format:
<VCN DNS label>.oraclevcn.comFor example:
companyabc.oraclevcn.comTip: If you want to connect to a private source on the same VCN as the private access channel, select the checkbox Virtual Cloud Network's Domain Name as DNS Zone on the Configure Private Access Channel page to auto-fill the domain name value.
-
Private Oracle Autonomous AI Lakehouse or Oracle Autonomous AI Transaction Processing in an Oracle Cloud Infrastructure VCN
The private FQDN hostname is in the format
<adb-name>.adb.<region>.<realm-public domain>.Register a DNS zone in the same format:<adb-name>.adb.<region>.<realm-public-domain>For example:
myadw.adb.ap-sydney-1.oraclecloud.commyadw.adb.uk-gov-cardiff-1.oraclegovcloud.uk
-
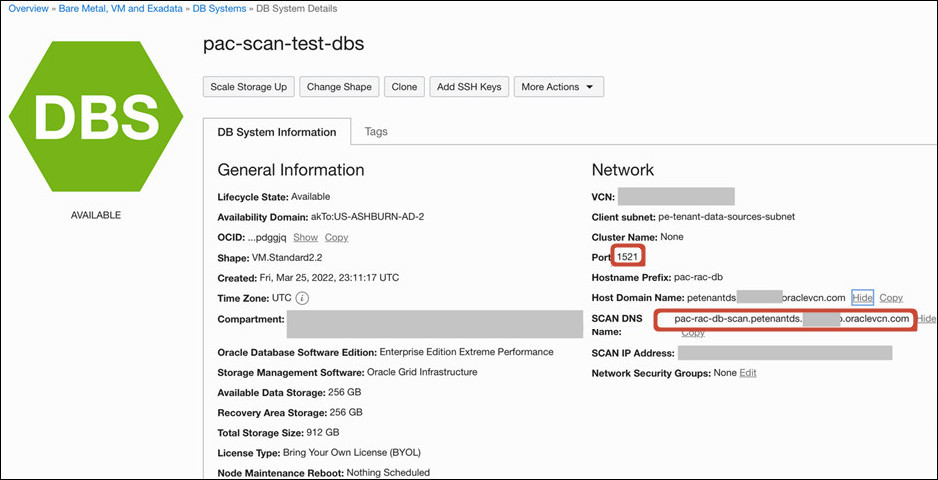
- Record the SCAN host name and SCAN port for each private Oracle Database
configured with a Single Client Access Name (SCAN) that you want Oracle
Analytics Cloud to access through the private channel. For example, SCAN host names such as
db01-scan.corp.example.comorprd-db01-scan.mycompany.commight use port 1521.If you want to connect to a private DB System on Oracle Cloud Infrastructure, you can find SCAN details on the DB System Information page (SCAN DNS Name and Port).
- Determine the Oracle Cloud
Infrastructure VCN and subnet that you want Oracle
Analytics Cloud to use for the private channel.
VCN Prerequisites
-
Region: The VCN must be in the same region as Oracle Analytics Cloud.
Subnet Prerequisites
-
Size: Each private access channel requires at least four IP addresses. Two IP addresses are required for network traffic egress, one IP address for the private access channel, and one reserved for future use. This means that the minimum subnet size for a single private access channel is "
/29". For example, subnet CIDR10.0.0.0/29.If you have more than one Oracle Analytics Cloud instance, you might need to configure multiple private access channels. If you want to use a single subnet for multiple channels, you must ensure that the subnet is sized accordingly. Alternatively, use a dedicated subnet for each private access channel.
-
Egress Rule: The subnet must include an egress rule that enables communication to the private data source (IP address and port).
-
Ingress Rule: The subnet must include an ingress rule that enables communication from the private data source.
If you're not sure, ask your network administrator.
VCN and subnet configuration tasks are typically performed by the network administrator responsible for the Oracle Cloud Infrastructure network. More information is available in Task 1 Set up the VCN and subnet at Scenario B: Private Subnet with a VPN or Scenario C: Public and Private Subnets with a VPN.
-
- Ensure that you (or whoever plans to configure the private access channel for
Oracle
Analytics Cloud) belongs to a group that is granted the required policies to access the
VCN.
Several options are available. Choose the most appropriate level for you:
Broad Resource Access Policy
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ compartments IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO MANAGE virtual-network-family IN TENANCY
Limited Resource Access Policy
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ compartments IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ virtual-network-family IN compartment <compartment name of VCN> -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO USE subnets IN compartment <compartment name of subnet> -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO MANAGE vnics IN compartment <compartment name of Analytics instance> -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO USE private-ips IN compartment <compartment name of Analytics instance>
Moderate Resource Access Policy - Option 1
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ compartments IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ virtual-network-family IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO USE subnets IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO MANAGE vnics IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO MANAGE private-ips IN compartment <compartment name of Analytics instance>
Moderate Resource Access Policy - Option 2
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ compartments IN TENANCY -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO USE virtual-network-family IN compartment <compartment name of VCN> -
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO MANAGE virtual-network-family IN compartment <compartment name of Analytics instance>
-
- If you plan to enable access to a data source with SCAN host and port details,
ensure that you (or whoever plans to configure the private access channel for
Oracle
Analytics Cloud) belongs to a group that is granted the required policy to access work
requests.
Choose the most appropriate level for you:
Broad Resource Access Policy
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ work-requests IN TENANCY
Limited Resource Access Policy
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO READ work-requests IN compartment <compartment name of Analytics instance>
-
- Optional: If you plan to restrict traffic over the private access channel using
network security group rules, you can do so when you create the
channel or you can save the task for later.
If you want to configure network security groups when you create the private access channel, make sure the network security groups exist and you have the required policies to use network security groups.
-
ALLOW GROUP <ANALYTICS ADMIN GROUP> TO USE network-security-groups IN TENANCY
-