Use Dedicated Vantage Points
You can set up a Dedicated Vantage Point to define a location within your own tenancy to run your monitors securely.
You can use a Dedicated Vantage Point to monitor applications behind a firewall or in a corporate network environment, which cannot be accessed by a public vantage point. The Dedicated Vantage Point cannot be used by anyone outside your tenancy and you have complete control over network settings. In this way, you can make a Dedicated Vantage Point a part of your corporate network and monitor endpoints that are not publicly accessible.
A Dedicated Vantage Point is an Application Performance Monitoring resource, which can be set up in a tenancy using the Oracle-provided APM Availability Monitoring Dedicated Vantage Point template available in the Oracle Cloud Infrastructure Resource Manager service. A template is a pre-built Terraform configuration used to deploy cloud resources in a common scenario. The APM Availability Monitoring Dedicated Vantage Point template can be used to provision the infrastructure and prerequisites for a Dedicated Vantage Point in Application Performance Monitoring. For more information on Resource Manager, see Overview of Resource Manager.
Here's an architecture diagram that provides an overview of a Dedicated Vantage Point within a secure network that includes a Virtual Cloud Network (VCN), and how it sends data from monitor runs to Application Performance Monitoring:
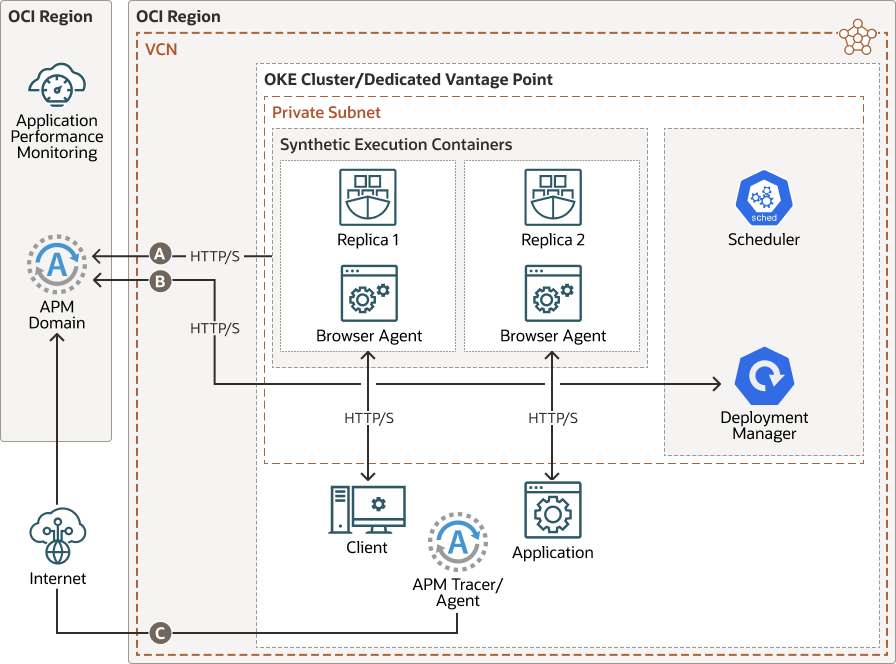
The following list describes the flow of data in the diagram:
- A – Metrics, HTTP Archive (HAR) files, and screenshots sent to the APM domain
- B – Flow of monitor configuration files and edits between the Deployment Manager and the APM domain
- C – Traces, spans, and metrics sent to the APM domain
Perform Dedicated Vantage Point Prerequisite Tasks
Here are the prerequisite tasks that must be performed before you set up a Dedicated Vantage Point.
| Task | More Information |
|---|---|
| Ensure that you have sufficient quota for the resources required to create a stack using the APM Availability Monitoring Dedicated Vantage Point template.
To check resource quota in the compartment in which the Dedicated Vantage Point will be set up:
|
For information on quota in Oracle Cloud Infrastructure, see Compartment Quotas. |
Ensure that the user setting up the Dedicated Vantage
Point has the permissions to access the Resource Manager service, create
a stack (resource-type: orm-stacks) and view jobs
(resource-type: orm-jobs), and create and access the
following resources.
Note that the VCN must be created manually and the other resources listed above are created as part of the Resource Manager stack. OKE Private Endpoints: In addition to
the above resources access, ensure the user has the permission to
create resource manager private endpoint, |
For information on policies, see:
For examples of the policies that must be created to grant a non-admin user the required permissions to create the Resource Manager stack, see perform-oracle-cloud-infrastructure-prerequisite-tasks.html#GUID-6F390B5F-DCF5-4299-A9E5-0C7F81A75E61__SECTION_ZG4_VW2_HTB. |
| Create a VCN and add the following security
rules:
For Oracle Kubernetes Engine (OKE) Public Endpoint:
For Oracle Kubernetes Engine (OKE) Private Endpoint:
|
For information on creating a VCN, see To create a VCN.
For information on security rules for the Kubernetes API endpoint, see Security Rule Configuration in Security Lists and/or Network Security Groups. |
| Ensure that an APM Domain is created and generate a
private data key for the Dedicated Vantage Point. The Dedicated Vantage
Point will be registered to the APM Domain and the private data key is
required to ensure that Application Performance Monitoring accepts the monitoring metrics and data collected by
the Dedicated Vantage Point. It's recommended that the name of the
private data key is in the following format:
|
For information on creating an APM Domain and generating data keys, see Create an APM Domain. |
| Generate an auth token to pull Dedicated Vantage Point artifacts from the Container Registry. | For information on generating an auth token, see Getting an Auth Token. |
Set Up a Dedicated Vantage Point
To set up a Dedicated Vantage Point using Resource Manager, you must create a stack using the APM Availability Monitoring Dedicated Vantage Point template.
Monitor Dedicated Vantage Points
After setting up a Dedicated Vantage Point, you can monitor the Dedicated Vantage Point.
To monitor a Dedicated Vantage Point:
- Navigate to the Availability Monitoring page.
- On the left pane, click Dedicated Vantage Points,
select the compartment in which you created the Dedicated Vantage Point, and the APM
Domain to which it's registered.
The Dedicated Vantage Point is listed.
- Click the name of the Dedicated Vantage Point.
The <name of the Dedicated Vantage Point> page is displayed.
- Review information such as the region, when the Dedicated Vantage Point was created, and so on. You can also perform actions such as adding tags or deleting the Dedicated Vantage Point. Note that if you delete the Dedicated Vantage Point, any monitor that is only running on the Dedicated Vantage Point will also be deleted. If the monitor is also running on other public or dedicated vantage points, then it will not be deleted.
- Scroll down to view Dedicated Vantage Point-related Metrics.
- Click Monitors under Resources on the left pane to view the monitors running on the Dedicated Vantage Point, if any.
Update an Existing Dedicated Vantage Point
You can update an existing Dedicated Vantage Point by updating the configuration of the Dedicated Vantage Point stack in Resource Manager.
Here are the steps to be performed to update a Dedicated Vantage Point:
- Create a stack using the latest APM Availability Monitoring Dedicated Vantage Point template. For information, see Set Up a Dedicated Vantage Point.
- On the Stack Details page of the newly created stack, click Plan to generate an execution plan (run a plan job). The new plan job is listed under Jobs. For information, see To generate an execution plan (run a plan job) in Managing Stacks and Managing Jobs.
- On the Job Details page of the plan job, click
Download Terraform Configuration to download the
Terraform configuration
.zipfile. For information, see To view jobs and job details in Managing Stacks and Managing Jobs. - Go to the Stacks page and for the Dedicated Vantage Point that you want to update, click the Edit option. For information, see To edit a stack in Managing Stacks and Managing Jobs.
- On the Stack Information page in the Edit
Stack wizard, update the configuration stack using the Terraform
configuration
.zipfile that you downloaded in step 3. For information, see To update the configuration for a stack in Managing Stacks and Managing Jobs.