Tagging Autonomous Database Cloud Resources
Tagging is a powerful foundational service for Oracle Cloud Infrastructure (OCI) that enables users to search, control access, and do bulk actions on a set of resources based on the tag.
Parent topic: Governance
Importance of Tagging
Using the Oracle Cloud Infrastructure (OCI) tagging system, you can tag resources as per your organizational scheme allowing you to group resources, manage costs, and give insights into usage. Tags also help you build a governance model around security and Maximum Availability Architecture (MAA). As your organization expands its cloud footprint, it can become challenging to keep track of the deployment architectures, security best practices, MAA, application tier, etc. Using metadata tags to identify workload attributes can help keep up with the security and availability of your tenancy without cost overruns.
To enable customers to manage OCI resources securely and cost-effectively, Oracle provides a set of pre-defined tags in line with best practices for tagging resources. These tags are grouped into two namespaces - The OracleStandard namespace and the OracleApplicationName namespace. You can think of a tag namespace as a container for your tag keys.
Consider a scenario where your organization has multiple cloud resources such as, Autonomous Container Databases, Autonomous Databases, compute, network and load balancers across multiple compartments in your tenancy. Suppose you wish to track these cloud resources for specific purposes, report on them, or take bulk actions. In that case, you will need a system that lets you group these resources based on different criteria such as environment, criticality, target users, application, etc. You can achieve this by applying appropriate tags to these resources.
For example, you may tag all resources in your development stack with Oracle-Standard.Environment=Dev or for a business critical application stack, set Oracle-Standard.Criticality=High or Extreme. In the event of service disruptions due to various reasons, you would then be able to quickly identify all OCI resources associated with an application or business function or be able to separate critical and non-critical workloads.
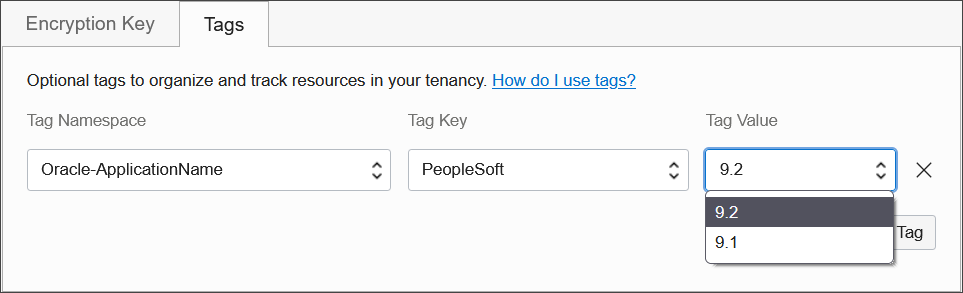
Tagging can also help you deploy optimized configurations based on workload attributes identified via tags. For example, database deployments for the Peoplesoft application require a specific configuration. By setting the ApplicationName and AppMajorVersion tags, while deploying an autonomous database, can ensure that the database is configured ready for the particular application (Example: Peoplesoft) out of the box.
Moreover, integration with the Cloud Advisor OCI service can provide you with direct, deep insight into how well your cloud services adhere to the corporate guidelines and help your management govern with a vision. See Cloud Advisor Overview for more details.
Parent topic: Tagging Autonomous Database Cloud Resources
Adding Tags
You can tag resources using the Oracle Cloud Infrastructure (OCI) console, command-line interface, or SDK.
There are many cloud resources that can be tagged in an Autonomous Database deployment. Exadata Infrastructure, Autonomous Exadata VM Cluster, Autonomous Container Database, and Autonomous Datatabase are some of them. Tags can either be applied while creating the resources or modified later. For example, you can apply tags to an Autonomous Container Database (ACD) while provisioning the ACD or add them later from its Details page.
See How Tagging Works for more details on using tags. Tagging integrates with Oracle Cloud Infrastructure authorization system. You can use IAM policy controls to enable delegation or restriction of tag manipulation. See Authentication and Authorization to learn about the permissions required to work with defined and free-form tags.(Required) Enter introductory text here, including the definition and purpose of the concept.
Tip:
For a "try it out" tutorial that demonstrates implementing tags in Oracle Autonomous Database on Dedicated Exadata Infrastructure, refer to Lab 14: Oracle Standard Tags in Oracle Autonomous Database Dedicated for Fleet Administrators Workshop on Oracle LiveLabs.Your tenancies come with a library of standard tags that would apply to most resources. These tags are currently available as a set of Tag Namespaces that your governance administrators can deploy. OCI best practices recommend applying these tags to all resources a standard tag can be applied to. Besides reporting and governance, OCI service automation can deliver workload-specific optimizations based on standard tag values.
For example, database deployments for the Peoplesoft application require a specific configuration. By setting the appropriate application tag key in the Oracle-ApplicationName tag namespace while deploying an Autonomous Database, can ensure that the database is configured ready for the particular application (Example: Peoplesoft) out of the box.
Parent topic: Tagging Autonomous Database Cloud Resources
Oracle Standard Tags
Your tenancy governance administrators can deploy the standard tags at the tenancy level and may also mark certain tags as required, thereby enforcing tags on resources in those compartments. The following are the standard tags defined in the namespace called OracleStandard.
| Tag Key | Tag Value Options | Description |
|---|---|---|
| OracleStandard.Criticality |
Extreme High Medium Low |
Enables tiering of resource in line with corporate application classification standards. Customer governance can use this tag for reporting and ensuring resources are configured as per the guideline for the tier they belong to. For example, a database resource with OracleStandard.Criticality set to Extreme or High may require the highest availability SLA, and may need to be configured with Autonomous Data Guard. |
| OracleStandard.Environment |
Dev Test Prod Pre-prod Staging Trial Sandbox User Testing |
Denotes a resource lifecycle. In the case of databases, it helps determine consolidation density, database distribution across containers, set maintenance plans, and manage clones. |
| OracleStandard.Sensitivity |
Public Internal Sensitive Highly Sensitive Extremely Sensitive |
An application or database classification tag. OracleStandard.Sensitivity set to Highly Sensitive may indicate that an access control list or certain Network Security Group (NSG) enforcement is mandatory to restrict access. |
| OracleStandard.Regulation | Refer to List of Compliance Regulations for values. |
Denotes one or more compliance regulations that a resource must adhere to. Tag administrators may add values to the list from the OCI Governance and Administration console. Refer to Using Predefined Values for more details. |
| OracleStandard.TargetUsers |
Public Customers Partners Company Division Department Workgroup |
Denotes the end users of a resource. Another form of resource classification that helps determine target users and allow governance teams to set corporate standards based on user or application type. |
| OracleStandard.EndUserCount |
1 10 100 1000 10000 100000 1000000 1000000 10000000 |
An approximate count of end-users. This tag helps determine the number of users impacted or blast radius during an availability or security event. This also help prioritize recovery efforts in the event of major outages affecting a large number of cloud resources. |
| OracleStandard.OwnerEmail | Free form tag. For example: john.smith@acme.com or app_support_grp@acme.com |
Denotes the email address of the resource owner. |
| OracleStandard.Org | HR, Finance, Marketing, Sales, Legal, R&D, Customer Support, Internal Support, Manufacturing |
Identifies the customer's line of business or department that owns or uses the resource. This may help with cost aggregation reports and determining usage across business units. Tag administrators may add relevant values to the list from the OCI Governance and Administration console. Refer to Using Predefined Values for more details. |
| OracleStandard.CostCenter | 12345, WebMarketing |
Freeform field for cost center. |
| OracleStandard.RecoveryTimeObjectiveMinutes | 0-10080 |
Time in minutes. Denotes the maximum time within which the resource is required to recover from a failure. |
| OracleStandard.RecoveryPointObjectiveMinutes | 0-1440 |
Time in minutes. Maximum data loss tolerance for a data store resource such as a database or a storage device. |
List of Compliance Regulations
The table below lists the valid values that you can apply for the OracleStandard.Regulation tag.| Regulation | Description |
|---|---|
| PCI DSS | Payment Card Industry Data Security Standard |
| HIPAA | Health Insurance Portability and Accountability Act |
| ISO | International Standards Organization |
| SOC1 | System and Organization Controls 1 |
| SOC 2 | System and Organization Controls 2 |
| FedRamp | Federal Risk and Authorization Management Program |
| GLBA | Gramm–Leach–Bliley Act |
| CCPA | California Consumer Privacy Act |
| SOX | Sarbanes Oxley |
| NIST | National Institute of Standards and Technology - Cyber Security |
| FISMA | Federal Information Security Management |
| HITECH | Health Information Technology for Economic and Clinical Health Act |
| FERPA | Family Educational Rights and Privacy Act ( Student privacy) |
| FACTA | Fair and Accurate Credit Transaction Act |
| Texas HB300 | Texas Medical Records Privacy Act |
| CIS | Center for Internet Security |
| CJIS | Criminal Justice Information Services Security Policy |
| C-TPAT | Customs-Trade Partnership Against Terrorism |
| COPPA | Children's Online Privacy Protection Act |
| PIPED Act, or PIPEDA | Personal Information Protection and Electronic Documents Act |
| GDPR | General Data Protection Regulation |
| PIPL | Personal Information Protection Law |
Parent topic: Tagging Autonomous Database Cloud Resources
Oracle Application Name Tags
The following are the application name tags defined in the namespace called Oracle-ApplicationName.
| Tag Key | Tag Value Options | Description |
|---|---|---|
| Hyperion |
11.2 11.1 |
Denotes the version of the Hyperion application. |
| JD_Edwards |
9.2 9.1 9.0 |
Denotes the version of the JD Edwards application. |
| Oracle_E-Business_Suite |
12.2 12.1 12.0 11i |
Denotes the version of the Oracle E-Business Suite application. |
| PeopleSoft |
9.2 9.1 |
Denotes the version of the Peoplesoft application. |
| Siebel |
8.2 8.1 |
Denotes the version of the Siebel application. |
| Other_Oracle_Application | Free form tag in string format. | Can be used to denote any application other than those listed above. You can enter the application name as a string value. |
Parent topic: Tagging Autonomous Database Cloud Resources