Restrict Access to an Instance
Restrict the networks that have access to your Oracle Integration instance by configuring an allowlist (formerly a whitelist). Only users from the specific IP addresses, Classless Inter-Domain Routing (CIDR) blocks, and virtual cloud networks that you specify can access the Oracle Integration instance.
For the Oracle Integration instance, configure the allowlist when you create the instance or after creating the instance.
Option 1 for Configuring Allowlists: Restrict Access to Oracle Integration Using the Self-service Allowlist Capabilities
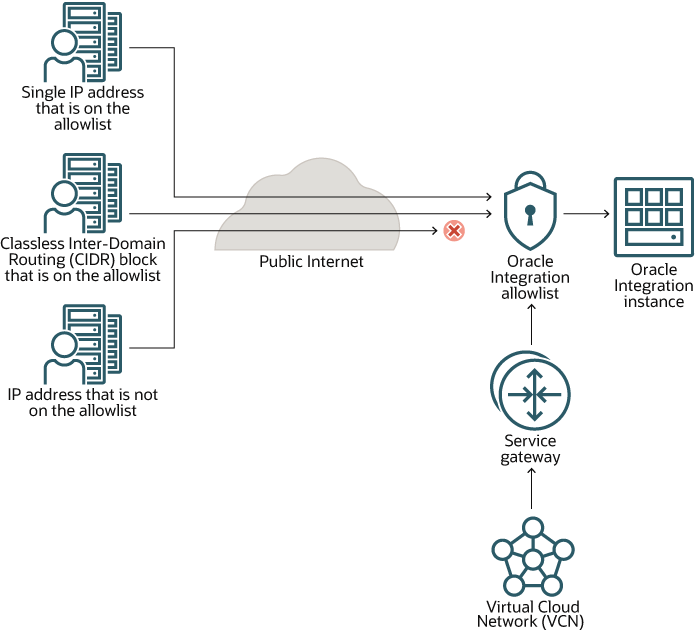
In this scenario, you restrict access to Oracle Integration using an allowlist. The allowlist restricts access based on the following parameters:
- Single IP address
- Classless Inter-Domain Routing (CIDR) block (that is, an IP address range)
- Virtual Cloud Network Oracle Cloud ID (VCN OCID)
Additionally, your organization might have a service gateway. The service gateway lets your virtual cloud network (VCN) privately access Oracle Integration without exposing the data to the public internet.
Only the specified IP addresses and VCN OCIDs can access Oracle Integration. Users and systems accessing Oracle Integration from listed VCNs have full access.
Advantages
- Easy setup! You can configure your allowlist in just a few minutes, without having to create a custom endpoint.
- All traffic is supported, including REST, SOAP, and other internet traffic.
Disadvantages
- The rules allow for all-or-nothing access and don't allow for more
nuanced control.
For instance, all traffic for a particular IP address or range is allowed, even if someone using an allowed IP address passes SQL as a command line parameter.
- You're limited to 15 access rules.
However, a CIDR block counts as only 1 entry, so you might not need more than 15 rules.
Tasks to Complete for this Scenario
- Add your organization's VCN OCID to the allowlist. The VCN must be
in the same region as Oracle Integration and should have
a service gateway.
When you add the VCN OCID to the allowlist, all resources on the VCN can access Oracle Integration.
- For all partner networks and applications, add their IP addresses or
address ranges to the allowlist.
You need all the IP addresses for all applications and systems that require access to Oracle Integration. Make sure you consider all partner systems and SaaS applications when compiling the list. For example, if a CRM platform requires access, you must add the individual or range of IP addresses for the platform.
When you add the IP addresses or address ranges to the allowlist, you grant full access to the user interface and integrations for your network.
- Enable loopback so that Oracle Integration can call itself.
For example, enabling loopback allows Oracle Integration to call its own REST APIs.
Option 2 for Configuring Allowlists: Restrict Access to Oracle Integration Using the Oracle Cloud Infrastructure Web Application Firewall (WAF)
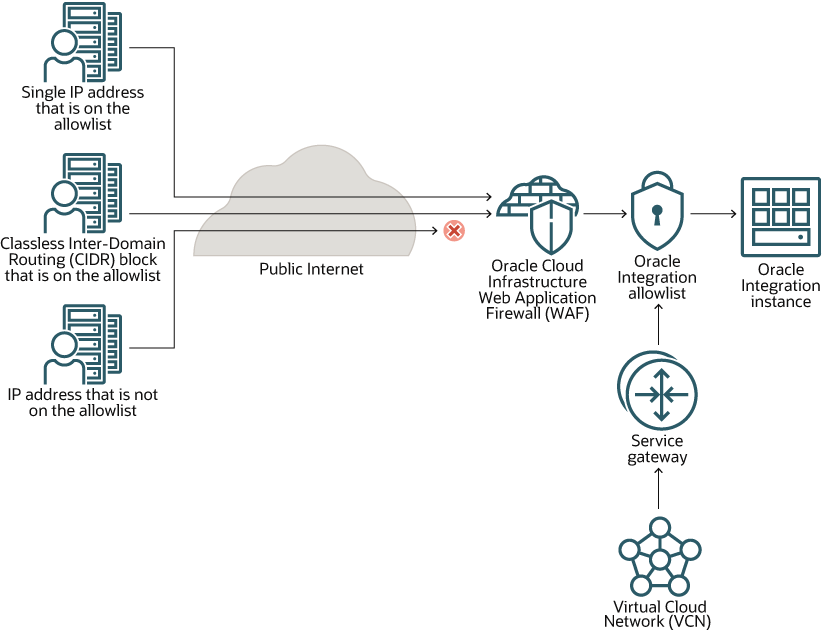
This scenario is the most powerful configuration option for allowlisting, allowing you to create sophisticated rules. In this scenario, you restrict access to Oracle Integration using Oracle Cloud Infrastructure Web Application Firewall (WAF).
How Each Item Controls Access
The allowlist lets the following entities access Oracle Integration:
- WAF
- Virtual Cloud Network Oracle Cloud ID (VCN OCID)
As a result, all internet traffic is routed to WAF, which restricts access based on:
- Single IP address
- Classless Inter-Domain Routing (CIDR) block (that is, an IP address range)
- Virtual Cloud Network Oracle Cloud ID (VCN OCID)
- Additional rules that you define
If your organization has a service gateway, the service gateway lets your virtual cloud network (VCN) privately access Oracle Integration without exposing the data to the public internet.
Advantages
- WAF allows you to create sophisticated rules for your allowlist. For
instance:
- If someone tries to pass SQL as a command line parameter, you can disallow the request.
- You can restrict access based on location using geo-blocking.
For more information, see Managing WAF Policies for Oracle Cloud Infrastructure Web Application Firewall.
- All traffic is supported, including REST, SOAP, and other internet traffic.
- The limitation of 15 allowlist rules doesn't apply to this scenario.
Disadvantages
- This option is more complex, time consuming, and error prone than the self-service allowlist on its own.
- You must create a custom endpoint for WAF, requiring a server certificate and a DNS entry.
Tasks to Complete for this Scenario
- Configure WAF according to your organization's requirements.
See Overview of Web Application Firewall for Oracle Cloud Infrastructure Web Application Firewall.
- Configure a custom endpoint for Oracle Integration.
- Add the IP address(es) for WAF to the allowlist.
If your organization has Oracle Integration in multiple regions, each region has its own WAF. You must add the IP addresses for all WAFs to the allowlist.
- Add your organization's VCN OCID to the allowlist. The VCN must be in the same
region as Oracle Integration and should have a service
gateway.
When the VCN OCID is on the allowlist, your virtual cloud network bypasses WAF.
You don't need to enable loopback when you use WAF to restrict access to Oracle Integration.
Option 3 for Configuring Allowlists: Restrict Access to Oracle Integration Using the API Gateway
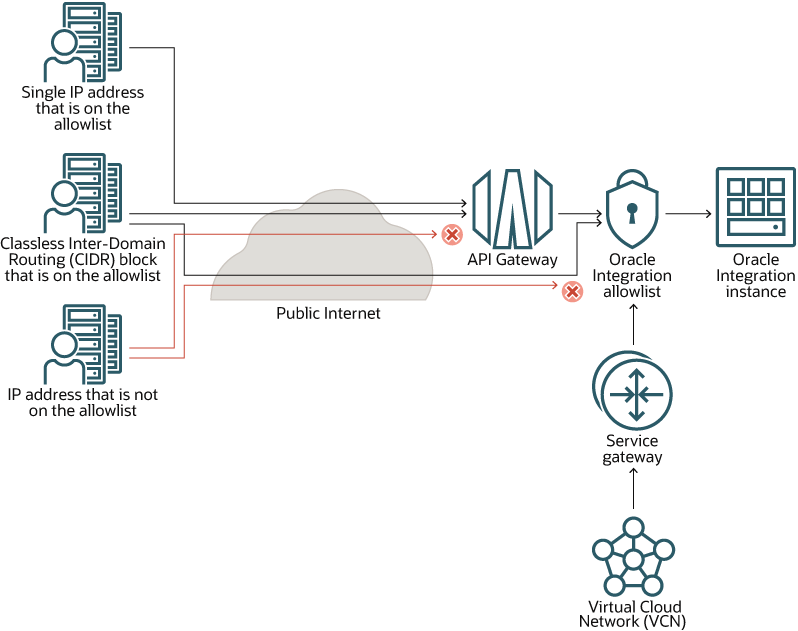
In this scenario, you restrict access to Oracle Integration using the API Gateway and and an allowlist.
If all traffic to Oracle Integration is in the form of REST API calls, this setup suits your needs. However, if you have traffic in the form of non-REST API calls, this scenario might not be ideal. You have traffic in the form of non-REST calls if your organization supports any of the following situations:
- Users working in the Oracle Integration user interface, including using Visual Builder and the Processes feature
- Users working in the Oracle Cloud Infrastructure Console user interface
- SOAP calls
If you support any non-REST calls, you must use the Oracle Integration allowlist to manage this access. Here's why: API Gateway doesn't let you add IP addresses to an allowlist.
How Each Item Controls Access
- All REST traffic from the internet is routed to API Gateway.
For details about how access is restricted, see Overview of API Gateway for API Gateway.
- The allowlist lets the following entities access Oracle Integration:
- API Gateway VCN
- Service gateway, if your organization has one
- REST and SOAP requests
Note
If you need Visual Builder and Processes access, this pattern allows for bypassing the API Gateway.
If your organization has a service gateway, the service gateway lets your virtual cloud network (VCN) privately access Oracle Integration without exposing the data to the public internet.
Advantages
- API Gateway allows you to create more nuanced rules than the
self-service allowlist.
See Adding Request Policies and Response Policies to API Deployment Specifications for API Gateway.
- The limitation of 15 allowlist rules doesn't apply to REST API calls.
Disadvantages
- If your organization uses File Server,
you can't restrict access using the API Gateway.
You'd have to allow direct access to File Server.
- This option is more complex, time consuming, and error prone than the self-service allowlist on its own.
- If you don't configure everything exactly as required, users experience access issues. For instance, users can't access the Processes feature, and only people on the internal network can access Visual Builder.
- For any non-REST calls to Oracle Integration, you must provide direct access using the Oracle Integration allowlist. You're limited to 15 access rules for this allowlist.
Tasks to Complete for this Scenario
You must complete these steps by hand and use the correct format, or users experience access issues.
- Configure API Gateway according to your organization's
requirements.
See the API Gateway documentation.
- Add your organization's VCN OCID to the allowlist. The VCN must be
in the same region as Oracle Integration.
When the VCN OCID is on the allowlist, your virtual cloud network bypasses the API Gateway
- Add API Gateway to the allowlist.
- Enable loopback so that Oracle Integration
can call itself.
For example, enabling loopback allows Oracle Integration to call its own REST APIs.
REST API for Allowlisting
You can also use the REST API for creating and modifying allowlists. See /integrationInstances/{integrationInstanceId}/actions/changeNetworkEndpoint.Prerequisites for Creating an Allowlist for Oracle Integration
When creating your allowlist, you must include all applications that require access to your instance. Here's the information you need.
These tasks are required for Oracle Integration.
Get the Outbound IP Addresses for Applications That Are Event Sources
You must add all event sources, such as Oracle Fusion Applications ERP events, to the allowlist. To do so, you must get the outbound IP address of the applications. Contact the application providers to get the IP addresses.
Get the Public IP Addresses for Oracle SaaS Applications That Make HTTPS Calls to Oracle Integration
Oracle SaaS applications can make HTTPS calls to Oracle Integration depending on the design of the integration. Go to the About menu in Oracle Integration to get the public IP address of your SaaS instance to add to the allowlist in Oracle Integration. See Obtain the NAT Gateway IP Address of the Oracle Integration Instance.
Some examples:
- Integrations using SaaS adapter connections for trigger and callbacks
- When the connectivity agent is used with an adapter that does polling, such as for database polling and invoking
- When the connectivity agent is used to communicate with Oracle Integration
For a list of external IP addresses by data center that you can add to your allowlist for web service calls initiated by Oracle Cloud Applications, see the support note ID 1903739.1: IP Whitelist for Web Service Calls Initiated by Oracle Cloud Applications .