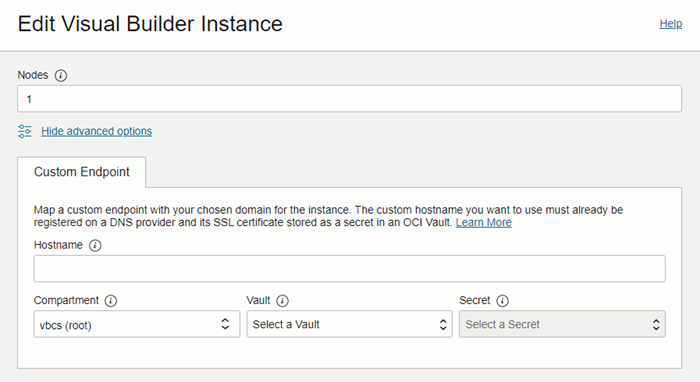
Create and Configure a Custom Endpoint
You can map a custom endpoint to a Visual Builder instance and use it to access the instance instead of the original URL generated in the OCI Console.
Let's say you want to open your Visual Builder instance from a custom URL like https://my-custom-endpoint.example.com/ic/builder instead of the original URL generated by Oracle (which can look something like https://<instance-display-name>-<tenancy-name>-<region-code>...oraclecloud.com). To do this, you create a hostname for your chosen custom domain (for example, my-custom-endpoint.example.org), and then create a custom endpoint in your Visual Builder instance that is associated with the hostname. Creating a custom endpoint doesn't affect the original instance URL of your Visual Builder instance. You'll be able to access your instance using the custom endpoint URL as well as the original instance URL.
If you are creating a custom endpoint for a private endpoint-enabled VB instance, and you want to make the custom endpoint public, you will need to use a public load balancer in your tenancy, and create a hostname, listener, and a backend that points to the private endpoint's IP address. This isn't needed if you don't intend to make the endpoint public.
After you have configured a custom endpoint, you can map an app in your instance to the endpoint by selecting the endpoint as the vanity URL in the settings of the visual application containing the app. After setting the app's vanity URL, users can and should open the app directly by entering the vanity URL root (https://my-custom-endpoint.example.com) in their browser. For more about using a vanity URL for an app, see Configure Support for a Custom Domain.
These instructions assume you have direct access to a Visual Builder instance and to the OCI Console.
To create and configure a custom endpoint for your Visual Builder instance: