Overview of Delegate Access Control
Learn how to delegate and maintain control over who has access to the delegated resources in your tenancy.
- What is Delegate Access Control?
Delegate Access Control service enables Oracle Exadata Database Service on Cloud@Customer and Oracle Exadata Database Service on Dedicated Infrastructure customers to subscribe to VM and database maintenance and support services, delegate access to service providers, and control when those service providers can access VM and database resources. - Terms Associated with Delegate Access Control
Learn about what terms are used with Delegate Access Control. - Strategic Customers Program for DB Cloud Platforms
The Strategic Customers Program for DB Cloud Platforms is an Oracle Service Provider designed to facilitate proactive service and operational management for ExaDB-C@C and ExaDB-D VM Clusters and databases. - Prerequisites
Review the prerequisites to configure and run Delegate Access Control. - Enforcement of Actions in Delegate Access Control
Learn about enforcing controls on the operations an Service Provider operator can perform in your environment.
What is Delegate Access Control?
Delegate Access Control service enables Oracle Exadata Database Service on Cloud@Customer and Oracle Exadata Database Service on Dedicated Infrastructure customers to subscribe to VM and database maintenance and support services, delegate access to service providers, and control when those service providers can access VM and database resources.
Delegate Access Control is a feature of the Operator Access Control Service and is included in attestations and advisories for Operator Access Control.
For more information on attestations and advisories, see Oracle Cloud Compliance.
Figure 1-1 Delegate Access Control Workflow
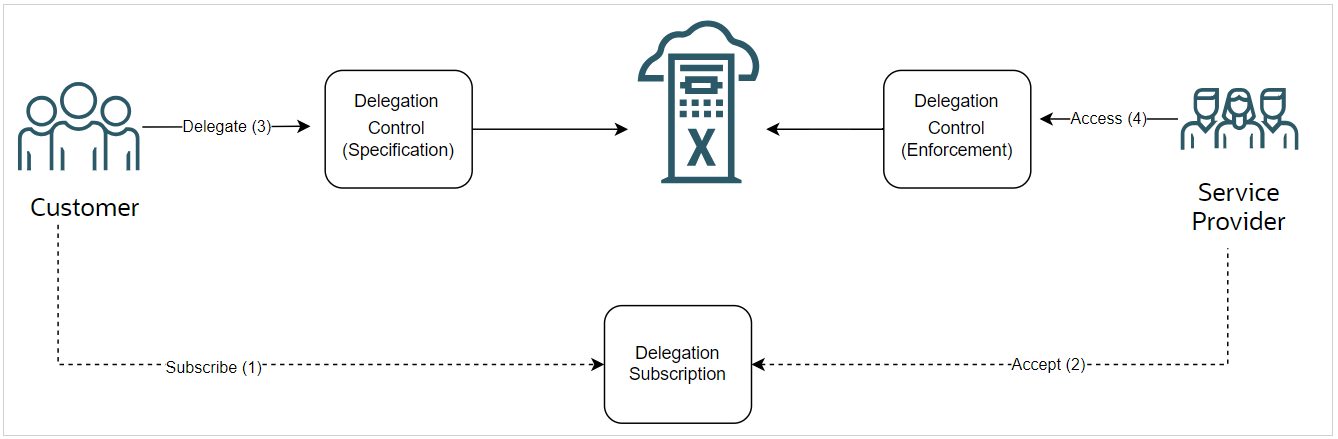
Delegated operators are specific to the support teams for the services that the VMs and databases are subscribed to. Available services include:
- Oracle Database Cloud Customer Support
- Oracle Database Cloud Operation
- Oracle Engineered Systems Deployment and Infrastructure Support
- Strategic Customers Program for DB Cloud Platforms
With Delegate Access Control, Support Providers can deliver managed services using comprehensive and robust tooling built on the OCI platform. Customers can maintain control over when the service provider delegates can access customer resources in their tenancy and what actions can be taken. Enterprises managing resources across multiple tenants can use Delegate Access Control to streamline management tasks.
Delegate Access Control allows Oracle Exadata Database Service on Cloud@Customer and Oracle Exadata Database Service on Dedicated Infrastructure customers to:
- Execute a "delegation subscription" with registered Support Providers, allowing them to take control of specified customer-owned resources. This ensures efficient and effective management by the Support Provider.
- Delegate access to their Exadata VMs (through SSH and API) to a Support Provider without having to maintain the Support Provider identities in customer IAM.
- View all delegated resources and the specific Support Provider(s) who can access the resource.
- Retain control over the scopes of delegation and the privileges given to the Support Provider operator when they access the delegated resource.
- Prevent Support Provider operators from accessing the delegated resource outside of the delegation control policy defined by the customer.
- Limit access duration to a predefined time.
- Audit all actions taken by the Support Provider operator on the delegated resources.
Delegate Access Control enables the support provider agents to:
- Gain access to delegated customer-owned systems (via SSH and API) without having to maintain their identities in the customer's IAM.
- See what resources have been delegated to the Support Provider by a customer.
Parent topic: Overview of Delegate Access Control
Terms Associated with Delegate Access Control
Learn about what terms are used with Delegate Access Control.
- Subscriber: This is the customer tenant who owns the resource and wants to delegate management of aspects of the resource to another tenant in OCI.
- Service Provider: This is the tenant who will be delegated access to the resource to manage it in a temporary fashion. There are two types of Service Providers
- Cloud service operators: They may access the delegated resources to troubleshoot issues. During maintenance activities, actions taken on infrastructure components can sometimes adversely affect processes running in the virtual machine. Currently, if such issues arise, Oracle must notify the customer via email (or another form of communication) through the Support Contact, which can be a slow process and may delay issue resolution by over a day.
To expedite this process, a workflow similar to Operator Access Control could be implemented. This would enable Cloud service operators to submit access requests for the customer’s VM. Access granted through this workflow would be limited to the defined scope of delegation and specified privileges, ensuring that operators are restricted from accessing the customer's database.
For more information about Operator Access Control, see Overview of Oracle Operator Access Control.
- Oracle support operators: The Oracle Support organization possesses extensive expertise in troubleshooting patching and performance issues with database software. Many of our marquee customers prefer to delegate access to their Exadata VMs for quarterly patching exercises. In addition, Oracle Platinum Support or Advanced Customer Support (ACS) is often engaged on an on-demand basis to troubleshoot issues.
In these scenarios, ACS engineers might need access to the customer’s VMs to perform various tasks:
- Quarterly Patching: Customers often wish to delegate the responsibility of patching their virtual machines (operating system, or Database, Grid Infrastructure) to ACS engineers.
- On-Demand Troubleshooting: When issues arise, ACS may need to access the customer’s database with varying levels of privilege:
- Low Privilege: Access restricted to performance and data dictionary views necessary for troubleshooting performance-related issues or other database problems.
- Moderate Privilege: Access that includes the ability to perform system patching.
This structured access ensures that ACS engineers can effectively address and resolve issues while respecting the customer’s security and operational boundaries.
- Cloud service operators: They may access the delegated resources to troubleshoot issues. During maintenance activities, actions taken on infrastructure components can sometimes adversely affect processes running in the virtual machine. Currently, if such issues arise, Oracle must notify the customer via email (or another form of communication) through the Support Contact, which can be a slow process and may delay issue resolution by over a day.
- Delegation Subscription: A resource can only be delegated to a provider after the customer has subscribed to a published service offered by that provider. Currently, the supported providers include:
- Oracle Database Cloud Customer Support
- Oracle Database Cloud Operation
- Oracle Engineered Systems Deployment and Infrastructure Support
- Strategic Customers Program for DB Cloud Platforms
- Delegation Control: This control policy governs how access to a delegated resource is managed. It determines whether access is granted automatically or requires a specific approval workflow. Delegation Controls must be associated with at least one delegation subscription. The policy includes enforcement for the following types of access to the delegated resource:
- Database Cloud Service API access
- SSH access
- Automation access
- On-demand remote VM level command access
- Delegated Resource: This is the resource governed by the delegation control set up by the customer, which the Provider can access. A Delegated Resource must be associated with only one Delegation Control.
- Delegated Resource Access Request: A Service Provider operator must raise a request for access before they can access a Delegated Resource. This request must be approved by an Approver, or it may be automatically approved based on the Delegation Control definition. An Access Request is always made from the Service Provider to the Subscriber.
- Access Request Approver: An Approver is a user in the Subscriber tenancy who has the authority to approve an Access Request raised by a Service Provider operator. If additional levels of approval are required for the Access Request, they can be configured during the creation of a Delegation Control.
- Service Provider Action (a.k.a. Action): A named, predefined set of commands, files, or network access permissions that can be granted on a specific resource as defined by Delegate Access Control.
Parent topic: Overview of Delegate Access Control
Strategic Customers Program for DB Cloud Platforms
The Strategic Customers Program for DB Cloud Platforms is an Oracle Service Provider designed to facilitate proactive service and operational management for ExaDB-C@C and ExaDB-D VM Clusters and databases.
The process begins with the Oracle team initiating an access request using the DLGT_MGMT_CMD_ACCESS action for a specific VM Cluster node, Grid Infrastructure, and databases. Once the customer approves the Delegated Resource Access Request, the Oracle team will perform collection activities using the Autonomous Health Framework (AHF). The process is non-intrusive, ensuring that customer systems remain fully operational and unaffected. Adhering to IAM policies, it enforces role-based access control with minimal privileges to safeguard customer environments. All actions are logged to ensure transparency and facilitate detailed audits.
These proactive services ensure that Oracle has the necessary insights into the client's systems to support planned activities effectively. By identifying potential issues in advance, Oracle helps clients mitigate risks and maintain optimal operational performance. The Strategic Customers Program emphasizes collaborative planning, timely response, and transparency, contributing to smoother client operations and a more resilient database infrastructure.
Parent topic: Overview of Delegate Access Control
Prerequisites
Review the prerequisites to configure and run Delegate Access Control.
- Types of installations: Customer VM Cluster in Exadata Database Service on Cloud@Customer (ExaDB-C@C) and Exadata Database Service on Dedicated Infrastructure (ExaDB-D)
Note
Exadata Database Service on Dedicated Infrastructure (ExaDB-D) with subnet using IPv6 is not supported due to limitation of Private Endpoint. - Oracle Exadata System Model: X8 and above
- Oracle Database Versions: Oracle Database releases 11.2.0.4 and above for log, backup, and configuration controls
- Customer VM Operating System: Oracle Linux 7 and above
- Service Provider Engagement: Before creating the Delegation Subscriptions in Delegate Access Control Service, engage with your desired Service Providers contractually to subscribe to their services:
- Oracle Database Cloud Customer Support
- Oracle Database Cloud Operation
- Oracle Engineered Systems Deployment and Infrastructure Support
- Strategic Customers Program for DB Cloud Platforms
- Allowlisting requirements in customer firewall/gateway:
- URL format:
https://dactlhe.exacc.$LONGREGIONNAME.oci.$TOPLEVELDOMAINReplace
$LONGREGIONNAMEwith the OCI region name, for example,us-ashburn-1Replace
$TOPLEVELDOMAINwith the OCI region domain, for example,oraclecloud.comFor example, the URL format for
ashbhurnregion will behttps://dactlhe.exacc.us-ashburn-1.oci.oraclecloud.com - Outbound port to allow: 443
- URL format:
- Network Security Rule to allow SSH to the VM Cluster for ExaDB-C@C and ExaDB-D
Ensure that SSH (port 22) is permitted on the client subnet of the VM Cluster for both ExaDB-C@C and ExaDB-D. This can be done using either a network security group or a security list in your VCN. Additionally, if Zero Trust Packet Routing policy is enabled for your VM Cluster, ensure that SSH traffic is allowed in both ingress and egress directions.
Here’s an example of a Zero Trust Packet Routing policy to allow SSH access within the client subnet of a Cloud VM Cluster:database:Prod-VMClusterrepresents the security attribute key and value for the Cloud VM Cluster.network:vm-cluster-vcnrepresents the security attribute key and value for the VCN.10.10.1.0/24is the CIDR block for the client subnet of the Cloud VM Cluster.
in network: vm-cluster-vcn VCN allow '10.10.1.0/24' to connect to database:Prod-VMCluster endpoints with protocol='tcp/22' in network: vm-cluster-vcn VCN allow database:Prod-VMCluster endpoints to connect to '10.10.1.0/24' with protocol='tcp/22'This policy ensures bidirectional SSH traffic (port 22) between the specified CIDR block and the VM Cluster, enforcing secure and restricted access using Zero Trust principles.
- Network Security Rule to allow the ExaDB-C@C and ExaDB-D VM Cluster to connect to other OCI services
Ensure that the ExaDB-C@C and ExaDB-D VM Cluster can connect to other OCI services using OCI Service Gateway at port 443. This can be done using either a network security group or a security list in your VCN. Additionally, if Zero Trust Packet Routing policy is enabled for your VM Cluster, ensure that
osn-services-ip-addressestraffic is allowed in both ingress and egress directions.Here’s an example of a Zero Trust Packet Routing policy to allowosn-services-ip-addressestraffic within the client subnet of a Cloud VM Cluster:database:Prod-VMClusterrepresents the security attribute key and value for the Cloud VM Cluster.network:vm-cluster-vcnrepresents the security attribute key and value for the VCN.osn-services-ip-addressesis the Oracle Service Network (OSN) IP addresses
in network: vm-cluster-vcn VCN allow osn-services-ip-addresses to connect to database:Prod-VMCluster endpoints with protocol='tcp/443' in network: vm-cluster-vcn VCN allow database:Prod-VMCluster endpoints to connect to osn-services-ip-addresses with protocol='tcp/443'This policy ensures that bidirectional traffic at port 443 between the OCI service and the Cloud VM Cluster is allowed explicitly, enforcing secure and restricted access in alignment with Zero Trust principles.
- IAM Policies for Delegate Access Control
- Applicable to both ExaDB-C@C and ExaDB-D
While the VM Cluster is in maintenance, there may be a delay in approving your access request. Selecting the "Auto-approve access requests during the maintenance window" option when creating a Delegation Control allows automatic approval during scheduled maintenance window to speed up the approval process. When Service Provider operators raise an access request, Delegate Access Control needs to check if the VM Cluster is in maintenance mode or not to auto-approve the request.
To allow Delegate Access Control to fetch information such as the lifecycle state, display name and compartment ID of the VM Cluster, DB Home, and database, create the following policy:allow any-user TO inspect database-family IN compartment <your compartment> where ALL { request.principal.type='dlgtmgmtdelegationcontrol' }<your compartment> is the compartment of the ExaDB-C@C and ExaDB-D VM Clusters and databases to be governed by Delegate Access Control.
Occasionally, Delegate Access Control will publish messages to customer through OCI Notification Service (ONS) to the ONS topic specified when creating the Delegation Control:- when an access request is waiting for approval
- when a duration extension of an access request is waiting for approval
- when an operator has responded to request for more information about an access request
To allow Delegate Access Control to publish messages to the ONS topic specified in the Delegation Control, create the following policy:allow any-user TO use ons-topics IN compartment <your compartment> where ALL { request.principal.type='dlgtmgmtdelegationcontrol' }<your compartment> is the compartment of the ONS topic specified in the Delegation Controls.
- Applicable to ExaDB-D
Delegate Access Control will access the Virtual Machines in the Cloud VM Cluster using SSH through Private Access. A SSH key pair is generated in the customer's OCI Vault specified when creating the Delegation Control. The SSH public key is then added to the Cloud VM Cluster.
To allow Delegate Access Control to read the private IP addresses of the Virtual Machines in the Cloud VM Cluster to create the Private Endpoint, create the following policy:allow any-user TO {PRIVATE_IP_READ} IN compartment <your compartment> where ALL { request.principal.type='dlgtmgmtdelegationcontrol' }<your compartment> is the compartment of the client subnet of the Cloud VM Cluster.
To allow Delegate Access Control to create the Private Endpoints to the Virtual Machines in the Cloud VM Cluster, create the following policy:allow any-user to use virtual-network-family IN compartment <your compartment> where ALL { request.principal.type='dlgtmgmtdelegationcontrol' }<your compartment> is the compartment of the client subnet of the Cloud VM Cluster.
To allow Delegate Access Control to read the SSH key in the OCI Vault to access the Virtual Machines in the Cloud VM Cluster, create the following policy:allow any-user TO read secret-bundles IN compartment <your compartment> where ALL { request.principal.type='dlgtmgmtdelegationcontrol' }<your compartment> is the compartment of the OCI Vault specified when creating the Delegation Control.
- Applicable to both ExaDB-C@C and ExaDB-D
- IAM Policies for Customer UserAll Delegate Access Control users should be given the following permissions by being a member of <your group>:
allow group <your group> to read delegation-management-service-providers in tenancyallow group <your group> to read delegation-management-service-provider-actions in tenancyallow group <your group> to read delegation-management-work-requests in compartment <your compartment><your compartment> is the compartment of the Delegate Access Control resources.
The user who will create, update, and delete Delegation Subscriptions needs to have the following permissions by being a member of <your group>:allow group <your group> to manage delegation-subscriptions in tenancyDelegation Subscriptions are not bound to a specific compartment; instead, they are created and managed in the root compartment.
The user who will create, update, and delete Delegation Controls needs to have the following permissions by being a member of <your group>:- To manage Delegate Access Control resources:
allow group <your group> to manage delegation-controls in compartment <your compartment><your compartment> is the compartment of the Delegation Controls.
- To create and store the SSH key pair in OCI Vault to access the Virtual Machines in the ExaDB-D Cloud VM Cluster:
allow group <your group> to manage secret-family in compartment <your compartment><your compartment> is the compartment of the OCI Vault specified in the Delegation Control.
- To have USE permission for the ExaDB-C@C VM Cluster and ExaDB-D Cloud VM Cluster:
allow group <your group> to USE database-family in compartment <your compartment><your compartment> is the compartment of the ExaDB-C@C VM Cluster and ExaDB-D Cloud VM Cluster.
The user who will approve, reject, revoke, and request more information about Delegated Resource Access Request needs to have the following permissions by being a member of <your group>:allow group <your group> to use delegated-resource-access-requests in compartment <your compartment><your compartment> is the compartment of the Delegated Resource Access Requests, which is the same compartment as the associated Delegation Control.
- To manage Delegate Access Control resources:
Parent topic: Overview of Delegate Access Control
Enforcement of Actions in Delegate Access Control
Learn about enforcing controls on the operations an Service Provider operator can perform in your environment.
- What is Action Enforcement?
The Service Provider Actions in Delegate Access Control limit the privileges an operator has when running commands, accessing resources, and changing the state of the system. - Action: Virtual Machine System Diagnostics
Virtual Machine System Diagnostics, identified asDLGT_MGMT_SYS_DIAG, enables Service Providers to gain SSH access to the customer's VM clusters with read access to log and diagnostic files. This action prevents access to sensitive information, system configuration changes, system restarts, and the audit system. - Action: Virtual Machine System Maintenance
Virtual Machine System Maintenance, identified asDLGT_MGMT_SYS_MAINT_ACCESS, enables Service Providers to gain SSH access to the VM clusters with limited privileges. - Action: Virtual Machine Full Access
Virtual Machine Full Access, identified asDLGT_MGMT_FULL_ACCESS, enables Service Providers to gain complete access to the VM clusters of the customers. - Action: Virtual Machine Command Access
Virtual Machine Command Access, identified asDLGT_MGMT_CMD_ACCESS, enables Service Providers to run a predefined set of commands on the VM clusters using REST APIs. Operators are not allowed SSH access to the VM clusters. - Action: Virtual Machine Log Access
Virtual Machine Log Access, identified as DLGT_MGMT_LOG_ACCESS, enables Service Providers to collect logs generated by DBaaS tools, database logs, and trace files on the VM clusters. - Action: Database Cloud Service (DBaaS) API Access
Database Cloud Service (DBaaS) API Access, which is identified asDLGT_MGMT_DBAAS_API_ACCESS, enables the Service Providers to gain access to a predefined set of OCI Database Cloud Service APIs to initiate patching or other database operations on behalf of the customers.
Parent topic: Overview of Delegate Access Control
What is Action Enforcement?
The Service Provider Actions in Delegate Access Control limit the privileges an operator has when running commands, accessing resources, and changing the state of the system.
An Action defines the permissions, resources, and system change access granted to a Service Provider operator to perform a specific range of tasks. These commands can include Oracle Linux commands or Oracle Database or Oracle Grid Infrastructure commands.
Resources that an Action grants access to include files and networks. System changes refer to state changes in the operating system or software running on those systems, often resulting from restarts or configuration modifications.
Action enforcement is based on approved Access Requests, which establish time-limited access for the Service Provider operator. Each access request creates a temporary user credential in the VM Cluster, with the scope of access defined by the Actions included in the approved access request.
Parent topic: Enforcement of Actions in Delegate Access Control
Action: Virtual Machine System Diagnostics
Virtual Machine System Diagnostics, identified as DLGT_MGMT_SYS_DIAG, enables Service Providers to gain SSH access to the customer's VM clusters with read access to log and diagnostic files. This action prevents access to sensitive information, system configuration changes, system restarts, and the audit system.
Operators use this action to triage or debug issues on the VM clusters by accessing diagnostics and log files. It does not allow operators to make any system changes or provide external network access.
This action provides read access to logs, including /var/log/messages. Most non-root commands will be available, but operators will not have the ability to use sudo to become any other user in the VM cluster.
Operator Privileges:
- Oracle Linux user privilege: Non-root
- Can su to root: No
- chroot jail: Yes
- Can su into: None
- Execute as root: No
- Network Privileges: No
Operator Privileges: System Commands
lscattaillessgreptoprpm(limited - allowed without the options to modify system)sha1sumwhowhichsed(limited - read/write only in user home and/tmp)cutawk(limited - read/write only in user home and/tmp)bccp(limited - user home to/tmp)mv(limited - user home to/tmp)rm(limited - user home to/tmp)rmdir(limited - user home to/tmp)touch(limited - user home to/tmp)find(limited folders only)filestat(limited folders only)tee(limited - user home and/tmp)datedudfheaddiff(limited folders only)sortjobsunamehostnamedirnamehistorymanechounzip(limited - user home and/tmp)chmod(limited - user home and/tmp)chown(limited - user home and/tmp)fgtputidgroupswhoamiwcxargsethtool(allowed without the options to modify interface parameters)lsoffuser
Certain commands are restricted, such as
rpm and ethtool. For these restricted commands, only arguments used for reading are permitted, not those used for writing. For instance, the -i option for rpm, which is used to install packages on the server, cannot be used.
Operator Privileges: Oracle Database and Oracle Grid Infrastructure Commands
The following commands are provided to operators for executing privileged operations through secure aliases. These aliases allow the execution of privileged operations in a read-only mode, without granting full access to the underlying utility.
$GRID_HOME/bin/crsctl --arguments(limited access, read-only)$ORACLE_HOME/bin/srvctl --arguments(limited access, read-only)imageinfoimagehistorylsnrctl --arguments(limited access, read-only)ocrcheck --arguments(limited access, read-only)ocrconfig --arguments(limited access, read-only)olsnodes --arguments(limited access, read-only)cluvfy --arguments(limited access, read-only)asmcmd --arguments(limited access, read-only)ocrcheck --arguments(limited access, read-only)get_dbnamesget_dbstatusget_dbenvdbaascli_diag_collecttfactl_diag_collecttfactl_print_statustfactl_get_defaultocimonitoringshow_tfa_blackoutsdgmgrl --arguments(limited access, read-only)rman --arguments(limited access, read-only)opatch --arguments(limited access, read-only)get_asmnames
Operator Privileges: Special Commands (owned by Delegate Access Control)
execsql: This command allows operator to run SQL queries in SQL*Plus console in restricted mode.info: This help command provides a brief description of the commands available in the cage.
Operator Privileges: Folder Permissions
-
Folder path:
/acfs01/Permission:
R -
Folder path:
/var/log/cellos/**Permission:
R -
Folder path:
/var/opt/oracle/**Permission:
R(limited to logs only -/var/opt/oracle/log,/var/opt/oracle/dbaas_acfs/log) -
Folder path:
/var/log/messagesPermission:
R -
Folder path:
/opt/oracle/dcs/logPermission:
R -
Folder path:
/opt/oracle/dcs/idempotencytoken_jobid_dbPermission:
R -
Folder path:
/u02/oracle.ahfPermission:
R -
Folder path:
/u02/app/oracle/diag/rdbmsPermission:
R -
Folder path:
/opt/oracle.ExaWatcher/archivePermission:
R -
Folder path:
/u01/app/grid/diagPermission:
R -
Folder path:
/var/log/cellosPermission:
R
Parent topic: Enforcement of Actions in Delegate Access Control
Action: Virtual Machine System Maintenance
Virtual Machine System Maintenance, identified as DLGT_MGMT_SYS_MAINT_ACCESS, enables Service Providers to gain SSH access to the VM clusters with limited privileges.
Service Providers can modify certain settings and restart components, including the database and Grid Infrastructure. Operators will not have the ability to use sudo as any other user in the VM cluster.
Operator Privileges:
- Oracle Linux user privilege: Non-root
- Can su to root: No
- chroot jail: Yes
- Can su into: None
- Execute as root: No
- Network Privileges: No
Operator Privileges: System Commands
lscattaillessgreptoprpm(limited - allowed without the options to modify system)sha1sumwhowhichsed(limited - read/write only in user home and/tmp)cutawk(limited - read/write only in user home and/tmp)bccp(limited - user home to/tmp)mv(limited - user home to/tmp)rm(limited - user home to/tmp)rmdir(limited - user home to/tmp)touch(limited - user home to/tmp)find(limited folders only)filestat(limited folders only)tee(limited - user home and/tmp)datedudfheaddiff(limited folders only)sortjobsunamehostnamedirnamehistorymanechounzip(limited - user home and/tmp)chmod(limited - user home and/tmp)chown(limited - user home and/tmp)fgtputidgroupswhoamiwcxargsethtool(allowed without the options to modify interface parameters)lsoffuser
Certain commands are restricted, such as
rpm and ethtool. For these restricted commands, only arguments used for reading are permitted, not those used for writing. For instance, the -i option for rpm, which is used to install packages on the server, cannot be used.
Operator Privileges: Oracle Database and Oracle Grid Infrastructure Commands
The following commands are provided to operators for executing privileged operations through secure aliases. These aliases allow the execution of privileged operations in a read-only mode, without granting full access to the underlying utility.
crsctllsnrctlsrvctltfactlcluvfy --arguments(limited access, read-only)ocrcheck --arguments(limited access, read-only)ocrconfig --arguments(limited access, read-only)olsnodes --arguments(limited access, read-only)asmcmd --arguments(limited access, read-only)service_driverbackup_apistart_tfactlstop_tfactlrestart_tfactldiagnosetfa_tfactlset_defaultocimonitoring_tfactlget_dbnamesget_dbstatusget_dbenvcleandblogs_gridcleandblogs_oracleimageinfoimagehistorydbaascli_diag_collecttfactl_diag_collecttfactl_print_statustfactl_get_defaultocimonitoringshow_tfa_blackoutsdatapatchopatchprechecksstopahf_ahfctlstartahf_ahfctlrestartahf_ahfctldgmgrl –arguments(limited access, read-only)rman --arguments(limited access, read-only)get_asmnamesdbasscli_admin_updatestackdbasscli_admin_showlateststackdbaascli_cswlib_showimagesdbaascli_system_getdatabasesdbaascli_system_getdbhomesdbaascli_system_getgridhomesdbaascli_database_rundatapatchdbaascli_dbhome_patchdbaascli_grid_patch
Operator Privileges: Special Commands (owned by Delegate Access Control)
execsql: This command allows operator to run SQL queries in SQL*Plus console in restricted mode.info: This help command provides a brief description of the commands available in the cage.
Operator Privileges: Folder Permissions
-
Folder path:
/acfs01/Permission:
R -
Folder path:
/var/log/cellos/**Permission:
R -
Folder path:
/var/opt/oracle/**Permission:
R(limited to logs only -/var/opt/oracle/log,/var/opt/oracle/dbaas_acfs/log) -
Folder path:
/opt/oracle/dcs/logPermission:
R -
Folder path:
/opt/oracle/dcs/idempotencytoken_jobid_dbPermission:
R -
Folder path:
/u02/oracle.ahfPermission:
R -
Folder path:
/u02/app/oracle/diag/rdbmsPermission:
R -
Folder path:
/opt/oracle.ExaWatcher/archivePermission:
R -
Folder path:
/u01/app/grid/diagPermission:
R -
Folder path:
/var/log/cellosPermission:
R
Parent topic: Enforcement of Actions in Delegate Access Control
Action: Virtual Machine Full Access
Virtual Machine Full Access, identified as DLGT_MGMT_FULL_ACCESS, enables Service Providers to gain complete access to the VM clusters of the customers.
This level of access is necessary in cases where the VM clusters exhibit highly intermittent issues. Full access grants operators the ability to use sudo as the root user, providing direct access to the original filesystem without any restrictions. Use sudo su to gain full access to the system.
Operator Privileges:
- Oracle Linux user privilege: Non-root
- Can su to root: Yes
- chroot jail: No
- Can su into: Yes
- Execute as root: Yes
- Network Privileges: Yes
Parent topic: Enforcement of Actions in Delegate Access Control
Action: Virtual Machine Command Access
Virtual Machine Command Access, identified as DLGT_MGMT_CMD_ACCESS, enables Service Providers to run a predefined set of commands on the VM clusters using REST APIs. Operators are not allowed SSH access to the VM clusters.
Operators will construct a JSON request and post it to the service endpoint.
{
"commandList": [
{
"command": "opatch",
"commandArguments": [
"lsinventory", "acstest"
]
}
]
}Operator Privileges:
- Oracle Linux user privilege: Non-root
- Can su to root: No
- chroot jail: Yes
- Can su into: None
- Execute as root: No
- Network Privileges: No
- SSH access: No
Operator Privileges: System Commands
lscattailgrepwhowhichtouch(limited - only to user home)find(limited folders only with full file name. No wild characters)datedudfhead(limited folders only)diff(limited folders only)jobsunamehostnamedirnamehistoryechoidgroupswhoami
Operator Privileges: Oracle Database and Oracle Grid Infrastructure Commands
The following commands are provided to operators for executing privileged operations through secure aliases. These aliases allow the execution of privileged operations in a read-only mode, without granting full access to the underlying utility.
start_tfactlstop_tfactlrestart_tfactlget_dbnamesget_dbstatusget_dbenvcleandblogs_gridcleandblogs_oracleimageinfoimagehistorydbaascli_diag_collectdatapatchruncollectionopatch
Operator Privileges: Special Commands (owned by Delegate Access Control)
info: This help command provides a brief description of the commands available in the cage.
Operator Privileges: Folder Permissions
-
Folder path:
/acfs01/Permission:
R -
Folder path:
/var/log/cellos/**Permission:
R -
Folder path:
/var/opt/oracle/**Permission:
R(limited to logs only -/var/opt/oracle/log,/var/opt/oracle/dbaas_acfs/log0 -
Folder path:
/opt/oracle/dcs/logPermission:
R -
Folder path:
/opt/oracle/dcs/idempotencytoken_jobid_dbPermission:
R -
Folder path:
/u02/oracle.ahfPermission:
R -
Folder path:
/u02/app/oracle/diag/rdbmsPermission:
R -
Folder path:
/opt/oracle.ExaWatcher/archivePermission:
R -
Folder path:
/u01/app/grid/diagPermission:
RExample:
/u02/app/oracle/product/19.0.0.0/dbhome_1/cfgtoollogs/opatch//u02/app/oracle/product/19.0.0.0/dbhome_2/cfgtoollogs/opatch/
-
Folder path:
/var/log/cellosPermission:
RExample:
/u02/app/oracle/product/19.0.0.0/dbhome_1/cfgtoollogs/opatch/lsinv/u02/app/oracle/product/19.0.0.0/dbhome_2/cfgtoollogs/opatch/
Parent topic: Enforcement of Actions in Delegate Access Control
Action: Virtual Machine Log Access
Virtual Machine Log Access, identified as DLGT_MGMT_LOG_ACCESS, enables Service Providers to collect logs generated by DBaaS tools, database logs, and trace files on the VM clusters.
These logs are uploaded to the Object Storage of the delegate access control service. The access to the diagnostic files in the Object Storage expires after a set number of days. The operator triggers log collection through a REST interface. A temporary user is created on the VM cluster with read-only access for log collection, and all logs are collected on behalf of this temporary user.
Operators will construct a JSON request and post it to the service endpoint.
{
"commandList": [
{
"command": "dlgtMgmtGetLogs",
"commandArguments": [
"/var/log/cellos/exwmetrics.log"
]
}
]
}Operator Privileges:
- Oracle Linux user privilege: Non-root
- Can su to root: No
- chroot jail: Yes
- Can su into: None
- Execute as root: No
- Network Privileges: No
- SSH access: No
Operator Privileges: System Commands
None
Operator Privileges: Oracle Database and Oracle Grid Infrastructure Commands
None
Operator Privileges: Special Commands (owned by Delegate Access Control)
None
Operator Privileges: Folder Permissions
-
Folder path:
/acfs01/Permission:
R -
Folder path:
/var/log/cellos/**Permission:
R -
Folder path:
/var/opt/oracle/**Permission:
R(limited to logs only -/var/opt/oracle/log,/var/opt/oracle/dbaas_acfs/log0 -
Folder path:
/opt/oracle/dcs/logPermission:
R -
Folder path:
/opt/oracle/dcs/idempotencytoken_jobid_dbPermission:
R -
Folder path:
/u02/oracle.ahfPermission:
R -
Folder path:
/u02/app/oracle/diag/rdbmsPermission:
R -
Folder path:
/opt/oracle.ExaWatcher/archivePermission:
R -
Folder path:
/u01/app/grid/diagPermission:
RExample:
/u02/app/oracle/product/19.0.0.0/dbhome_1/cfgtoollogs/opatch//u02/app/oracle/product/19.0.0.0/dbhome_2/cfgtoollogs/opatch/
-
Folder path:
/var/log/cellosPermission:
RExample:
/u02/app/oracle/product/19.0.0.0/dbhome_1/cfgtoollogs/opatch/lsinv/u02/app/oracle/product/19.0.0.0/dbhome_2/cfgtoollogs/opatch/
Parent topic: Enforcement of Actions in Delegate Access Control
Action: Database Cloud Service (DBaaS) API Access
Database Cloud Service (DBaaS) API Access, which is identified as DLGT_MGMT_DBAAS_API_ACCESS, enables the Service Providers to gain access to a predefined set of OCI Database Cloud Service APIs to initiate patching or other database operations on behalf of the customers.
allow any-user TO {CLOUD_VM_CLUSTER_UPDATE, CLOUD_EXADATA_INFRASTRUCTURE_UPDATE, VM_CLUSTER_UPDATE, EXADATA_INFRASTRUCTURE_UPDATE, EXADATA_INFRASTRUCTURE_INSPECT } IN tenancy where ALL { request.principal.type='dlgtmgmtresourceaccessrequest', request.principal.targetResourceId=target.resource.id }
allow any-user TO {DB_HOME_UPDATE, DB_HOME_INSPECT } IN tenancy where ALL { request.principal.type='dlgtmgmtresourceaccessrequest', request.principal.targetResourceId=target.resource.parent.id }Operator Privileges: Patching DBHome
Operator Privileges: VM Cluster Updates (Grid Patching / OS Updates)
- ListExadataInfrastructures
- ListVmClusters
- ListVmClusterUpdates (Update type: GI Upgrade, GI Patch, GI Update)
- UpdateVmCluster
- ListCloudExadataInfrastructures
- ListCloudVmClusters
- ListCloudVmClusterUpdates (Update type: GI Upgrade, GI Patch, GI Update)
- UpdateCloudVmCluster
The DBaaS APIs and IAM policy are specific to assisted patching. To run the DBaaS APIs in your tenancy, first add the IAM policy.
Parent topic: Enforcement of Actions in Delegate Access Control