Create Users on Autonomous AI Database
There are several options to create users on Autonomous AI Database. You can use Oracle Database Actions Database Users card or use client-side tools that connect to the database to create database users.
- Create Users on Autonomous AI Database with Database Actions
You can quickly create Autonomous AI Database users with Database Actions. - Create Users on Autonomous AI Database - Connecting with a Client Tool
You can create users by connecting to the database as the ADMIN user using any SQL client tool. - Unlock User Accounts on Autonomous AI Database
If a user account is locked, as the ADMIN user you can unlock the account. - About User Passwords on Autonomous AI Database
Autonomous AI Database requires strong passwords; the password you specify for a user must meet the minimum default password complexity rules. - Manage the Administrator Account on Autonomous AI Database
The administrator user for Autonomous AI Database is ADMIN, and this administrator account has several system privileges granted to be able to manage users and other areas of the database.
Parent topic: Manage Users
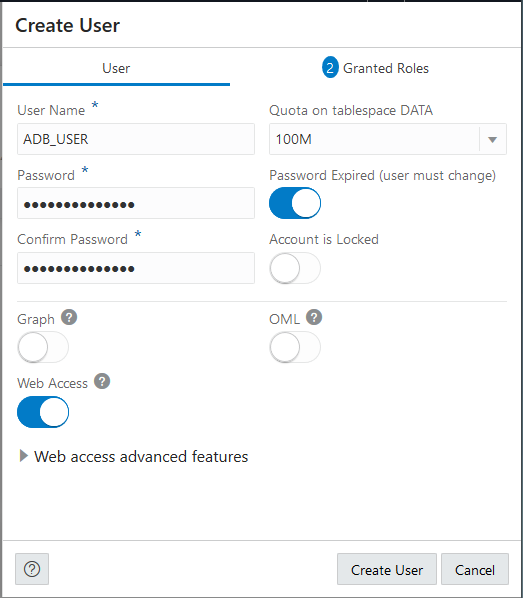
Create Users on Autonomous AI Database with Database Actions
You can quickly create Autonomous AI Database users with Database Actions.
First, access Database Actions as the ADMIN user. See Access Database Actions as ADMIN for more information.
See Manage User Roles and Privileges on Autonomous AI Database for more information on granting roles and adding or updating privileges for a user.
See The Database Users Page for detailed information on Database Actions Database Users.
If you provide Web Access for the new user, then you need to send a URL to the new user. See Provide Database Actions Access to Database Users for more information.
The administrator needs to provide the credentials wallet to the new user for client-side access. See Connect to Autonomous AI Database for more information on client-side access credentials.
Autonomous AI Database requires strong passwords; the password you specify must meet the default password complexity rules. See About User Passwords on Autonomous AI Database for more information.
See Create Oracle APEX Workspaces in Autonomous AI Database for information on creating APEX workspaces.
See Create and Update User Accounts for Oracle Machine Learning Components on Autonomous AI Database to add user accounts for Oracle Machine Learning Notebooks.
Parent topic: Create Users on Autonomous AI Database
Create Users on Autonomous AI Database - Connecting with a Client Tool
You can create users by connecting to the database as the ADMIN user using any SQL client tool.
For example, connect using Oracle SQL Developer (see Connect Oracle SQL Developer with a Wallet (mTLS)).
This creates new_user with connect privileges. This user can
now connect to the database and run queries. To grant
additional privileges to users, see Manage User Roles and Privileges on Autonomous AI Database.
The administrator needs to provide
the credentials wallet to the user
new_user. See Connect to Autonomous AI Database
for more information on client credentials.
Autonomous AI Database requires strong passwords; the password you specify must meet the default password complexity rules. See About User Passwords on Autonomous AI Database for more information.
See Provide Database Actions Access to Database Users to add users for Database Actions.
See Create Oracle APEX Workspaces in Autonomous AI Database for information on creating APEX workspaces.
See Create and Update User Accounts for Oracle Machine Learning Components on Autonomous AI Database to add user accounts for Oracle Machine Learning components.
Parent topic: Create Users on Autonomous AI Database
Unlock User Accounts on Autonomous AI Database
If a user account is locked, as the ADMIN user you can unlock the account.
To unlock an account, connect to your database as the ADMIN user and run the following command:
ALTER USER username IDENTIFIED BY password ACCOUNT UNLOCK;See SQL Language
Reference for information on the
ALTER USER command.
Parent topic: Create Users on Autonomous AI Database
About User Passwords on Autonomous AI Database
Autonomous AI Database requires strong passwords; the password you specify for a user must meet the minimum default password complexity rules.
Autonomous AI Database sets minimum standards for passwords, and the default profile sets parameters to limit the number of failed login attempts.
-
The password must be between 12 and 30 characters long and must include at least one uppercase letter, one lowercase letter, and one numeric character.
Note, the password limit is shown as 60 characters in some help tooltip popups. Limit passwords to a maximum of 30 characters.
-
The password cannot contain the username.
-
The password cannot be one of the last four passwords used for the same username.
-
The password cannot contain double quotation marks (") or single quotation marks (').
-
The password must not be the same password that is set less than 24 hours ago.
To change the password complexity rules and password parameter values you can alter the default profile or create a new profile and assign it to users. See Manage User Profiles with Autonomous AI Database for more information.
The following are the Autonomous AI Database default profile password parameter values:
| Password Parameter | Description | Value |
|---|---|---|
FAILED_LOGIN_ATTEMPTS |
The maximum times a user can try to log in and fail before locking the account. This limit applies for regular database user accounts. |
10 |
PASSWORD_GRACE_TIME |
The number of days after the grace period begins during which a warning is issued and login is allowed. |
30 |
PASSWORD_LIFE_TIME |
The number of days the same password can be used for authentication. |
360 |
PASSWORD_LOCK_TIME |
The number of days an account will be locked after the specified number of consecutive failed login attempts. |
1 |
PASSWORD_REUSE_MAX |
The number of password changes required before the current password can be reused. |
4 |
PASSWORD_REUSE_TIME |
The number of days before which a password cannot be reused. |
1 |
See Manage User Profiles with Autonomous AI Database for information on using CREATE USER or ALTER
USER with a profile clause.
See SQL
Language Reference for information on the ALTER USER
command.
Parent topic: Create Users on Autonomous AI Database
Manage the Administrator Account on Autonomous AI Database
The administrator user for Autonomous AI Database is ADMIN, and this administrator account has several system privileges granted to be able to manage users and other areas of the database.
You can change the administrator user (ADMIN) password and when locked, unlock the administrator user account on Autonomous AI Database. When you use the APIs to create an Autonomous AI Database or to reset the ADMIN password, you can optionally use an Oracle Cloud Infrastructure Vault secret to store the password.
See CreateAutonomousDatabase for more information.
See ADMIN User Roles and Privileges for more information on the ADMIN user.
- Set the ADMIN Password in Autonomous AI Database
Provides the steps to set the ADMIN password. - Unlock the ADMIN Account in Autonomous AI Database
Shows the steps to unlock the ADMIN user account. - Use Oracle Cloud Infrastructure Vault Secret for ADMIN Password
When you create or clone an Autonomous AI Database instance or when you reset the ADMIN password, you can use an Oracle Cloud Infrastructure vault secret to specify the ADMIN password.
Parent topic: Create Users on Autonomous AI Database
Set the ADMIN Password in Autonomous AI Database
Provides the steps to set the ADMIN password.
From the Oracle Cloud Infrastructure Console, change the password for the ADMIN user by following these steps:
- On the Details page, from the More actions drop-down list, select Administrator password.
- On the Administrator password panel enter the new password and confirm.
- Click Change.
You can also use Database Actions to change the password for the ADMIN user. See Manage Users and User Roles on Autonomous AI Database - Connecting with Database Actions for more information.
The password for the default administrator account, ADMIN, has the same password complexity rules mentioned in the section About User Passwords on Autonomous AI Database.
Unlock the ADMIN Account in Autonomous AI Database
Shows the steps to unlock the ADMIN user account.
Perform the following prerequisite steps as necessary:
-
Open the Oracle Cloud Infrastructure Console by clicking the
 next to Cloud.
next to Cloud.
- From the Oracle Cloud Infrastructure left navigation menu click Oracle Database and then click Autonomous AI Database.
-
On the Autonomous AI Databases page select an Autonomous AI Database from the links under the Display name column.
Use the following steps to unlock the ADMIN account by updating the ADMIN password:
- On the Details page, from the More actions drop-down list, select Administrator password.
- On the Administrator password enter the new password and confirm.
- Click Change.
This operation unlocks the ADMIN account if it was locked.
The password for the default administrator account, ADMIN, has the same password complexity rules mentioned in the section About User Passwords on Autonomous AI Database.
Use Oracle Cloud Infrastructure Vault Secret for ADMIN Password
Autonomous AI Database allows you to use the APIs to provide a protected vault secret as the ADMIN password, with secure access to the vault secret granted through Oracle Cloud Infrastructure IAM policies.
Using an Oracle Cloud Infrastructure vault secret for the ADMIN password is only supported with the APIs.
Oracle Cloud Infrastructure Vault secrets are credentials that you use with Oracle Cloud Infrastructure services. Storing secrets in a vault provides greater security than you might achieve storing them elsewhere, such as in code or in configuration files. By calling database APIs you can use secrets from the Vault Service to set the ADMIN password. The vault secret password option is available when you create or clone an Autonomous AI Database instance, or when you set or reset the ADMIN password.
You create secrets using the Oracle Cloud Infrastructure Console, CLI, or API.
Notes for using a vault secret to set or reset the ADMIN password:
-
In order for Autonomous AI Database to reach the secret in a vault, the following conditions must apply:
-
The secret must be in
currentorpreviousstate. -
If you specify a secret version in the API call, the specified secret version is used. If you do not specify a secret version, the call uses the latest secret version.
-
You must have the proper user group policy that allows
READaccess to the specific secret in a given compartment. For example:Allow userGroup1 to read secret-bundles in compartment training
-
-
The password stored in the secret must conform to Autonomous AI Database password requirements.
See the following for more information: